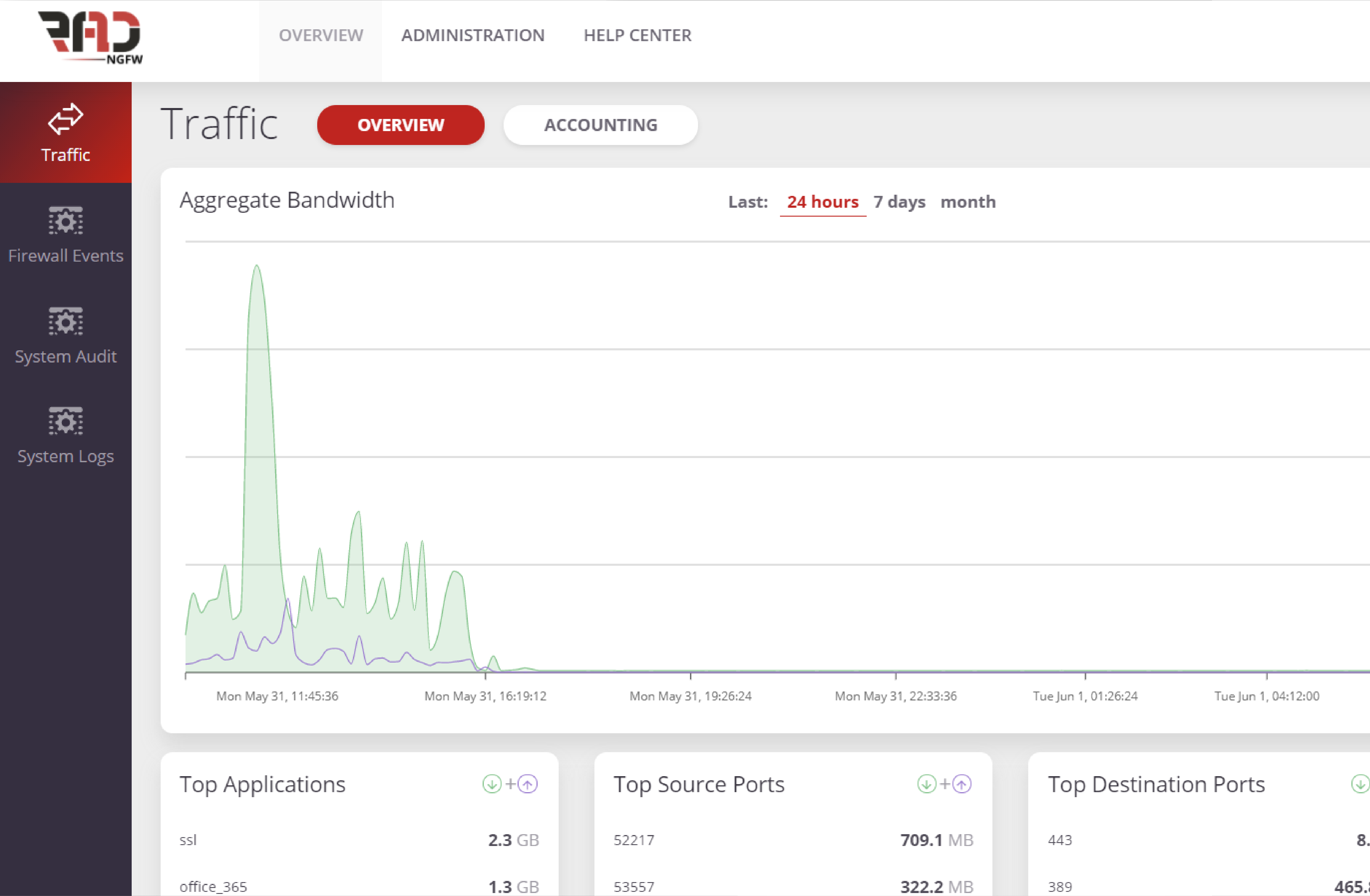
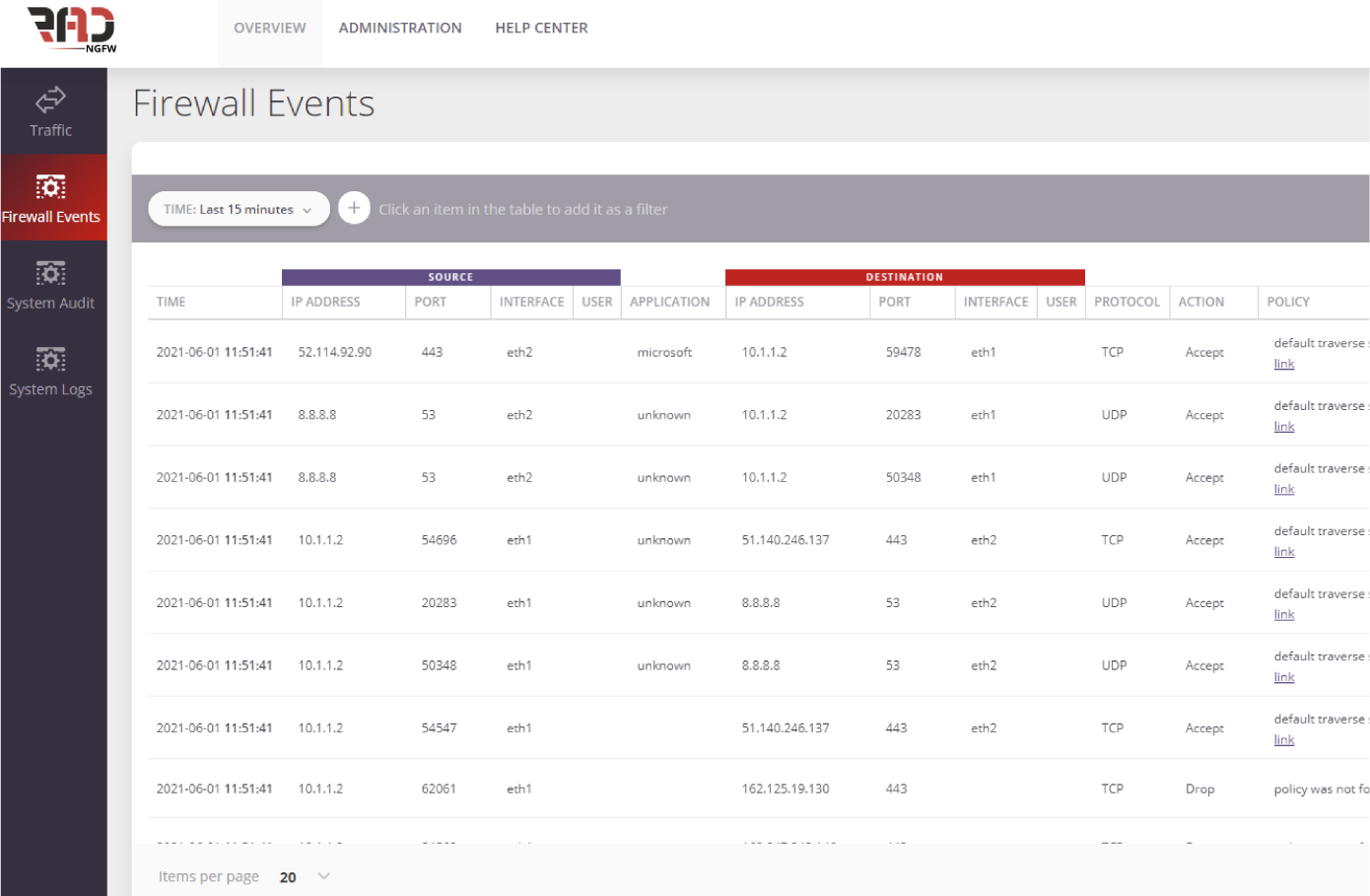
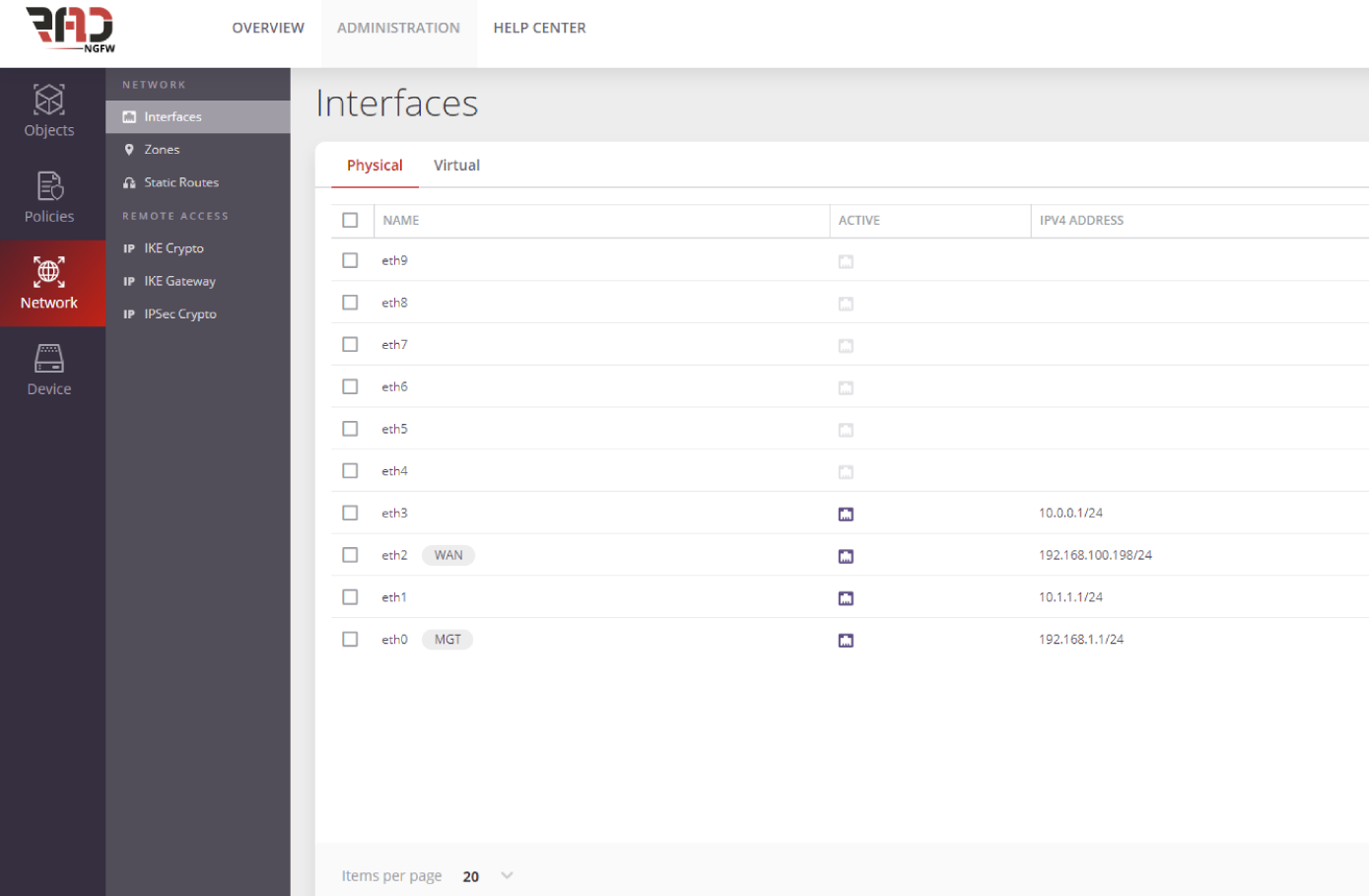
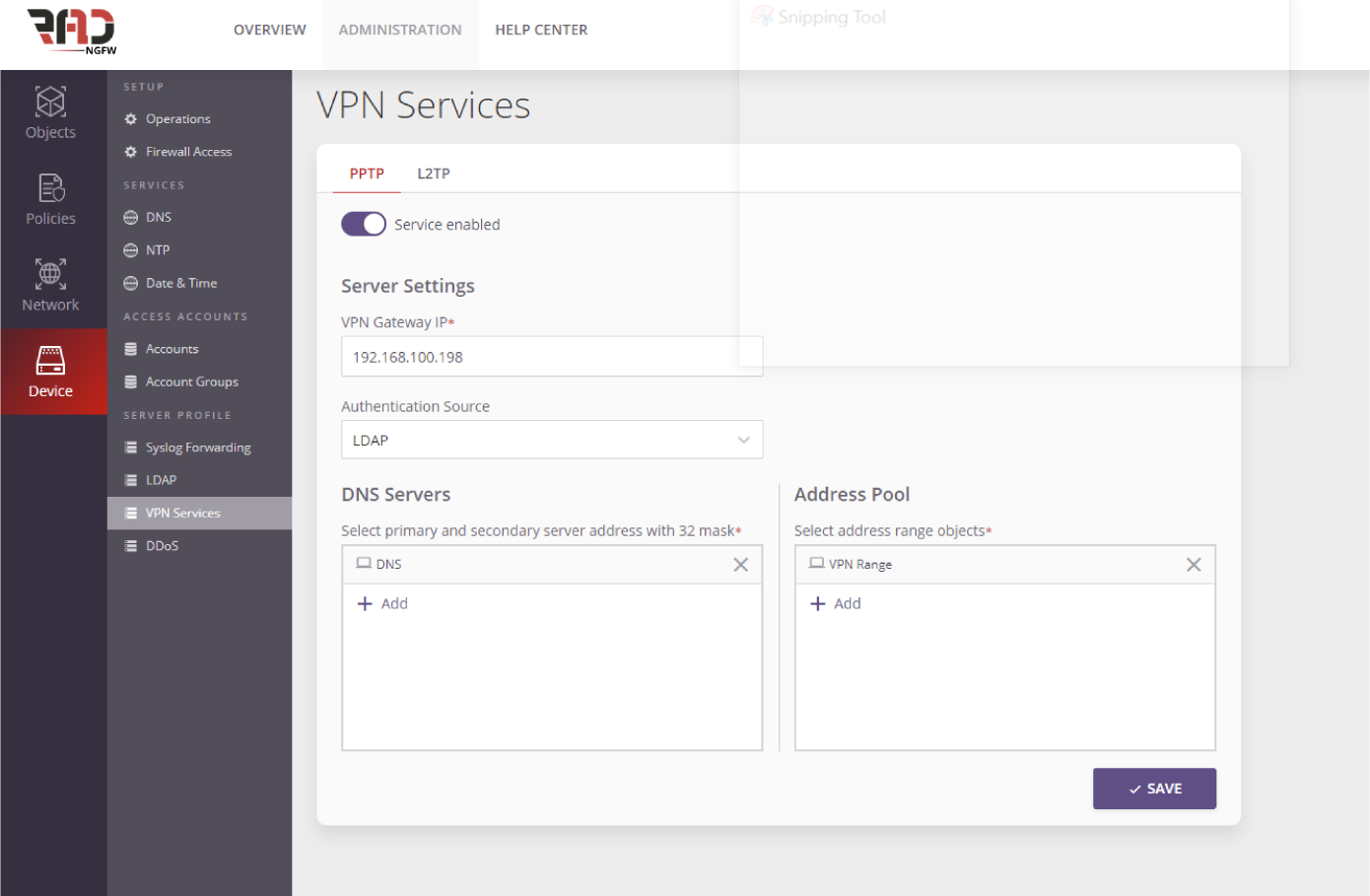
Identity-Based and User-Level Protection
Our identity-based policy technology secure and protect the network by granting the ability to control users access to applications, ports and other resources over network, regardless of device location, network, IP address or type of device.